![]()
Malware along with the normal traffic is a serious problem so analyzing or going deep in it will help to ensure that data is safe and you are connected to valid and secure servers. This post is all about analyzing the DNS protocol which is a application layer protocols and how its behavior changes by adding anomaly data to it. You must understand the header format of DNS and also must be familiar with the wire shark which analyze the data captured while browsing. AI Sangam has made the video on it where the real time implementation is done suing Keras and Tensorflow and accuracy of 70% is achieved. I am providing here the link. Please visit the link and don’t forget to watch the video on intrusion detection for DNS Protocol.
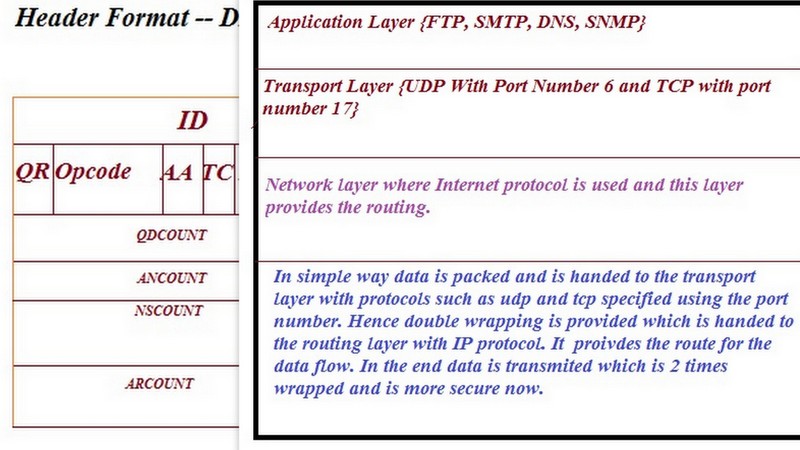
First of all one should know how packet or data is transmitted using different layer protocol. I am attaching below figure to explain you better.
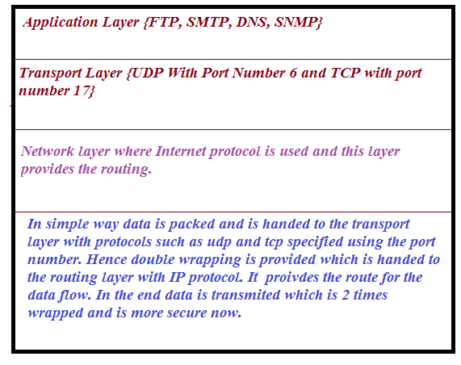
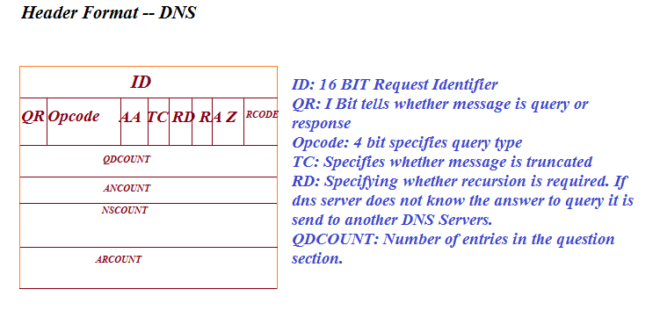
Data or Query in the DNS is analyzed because some times for one query, there may come many request which can be malware in the DNS Protocol. So it is very important to know whether you are getting the response from the right server because bad connection can make your data and information unsafe. Please refer the next figure to know more about DNS Header format.
Features used for training.
Following features are chosen for DNS packet for feeding the machine
- Length of Packet
- Source
- Destination
- Time to Leave
- Query Flag
- Zero
- RCODE
- SUM
- TCP_UDP
Model Used: At the backend Tensorflow is used and Keras is used along with it because it is easy to work with Keras. Model is trained with the above features and target contains 2 values. Value 0 if the traffic is normal and 1 if traffic contains malicious or malware.
Performance evaluation: When the real time testing is done on the data, accuracy comes out to be around 70%. This is good level of accuracy. Deep learning with sequential model is used. Sigmoid and Relu functions are used as an activation function.
Please watch the video whose link is provided at the top or you can click on link on Intrusion detection using keras and Tensorflow.